What are HTTP Security Headers?
When a user visits a website, its hosting server’s first reaction is HTTP response headers.
Some of these response headers are HTTP security headers. They instruct the visitor’s browser onhow to act during further interaction with the website. Some headers tell the browser to restrict those behaviors that are dangerous, but will not be used in a WordPress/ClassicPress website.
Implementing the right headers is a crucial security measure of a hosting setup. Without it, your website’s resilience to many common attacks, including dangers like cross-site scripting (XSS) and click-jacking, is dramatically weakened. In fact, a website without appropriate HTTP security headers can not be considered safe at all.
A few other HTTP response headers are indirectly related to privacy and security, so they can be considered HTTP security headers too.
Let’s look at what HTTP security headers you should expect from a decent WordPress/ClassicPress hosting provider.
Mandatory security headers

Source: infosecinstitute.com
In WordPress/ClassicPress hosting, some security headers are mandatory. Yes, you can go without them, but if you do, you will miss the very basics of web security. The very very basic.
Following is a list of headers that should be in a properly configured WordPress/ClassicPress hosting server.
HTTP Strict Transport Security (HSTS)
The HTTP Strict Transport Security (HSTS) header tells web browsers that your website uses HTTPs and should not be loaded using an insecure HTTP protocol. If you have moved your website from HTTP to HTTPs, this security header prevents browsers from loading your website on insecure HTTP protocol.
X-XSS Protection
The X-XSS Protection header blocks cross-site scripting from loading on your WordPress website.
X-Frame-Options
The X-Frame-Options security header prevents cross-domain iframes or click-jacking.
X-Content-Type-Options
The X-Content-Type-Options blocks content mime-type sniffing.
Recommended security headers
Content Security Policy (CSP) is an effective measure to protect your site from XSS attacks. It allows you to precisely control permitted content sources and many other parameters. However in WordPress, because of some plugins, it can break your website.
We recommend trying to add it manually in a staging (development) environment and checking if it breaks your website. If not, port it to the production website. If it breaks, sorry, you will have to live without it or find a plugin, which breaks your website and try to fix it.
Just be aware that sometimes in the WordPress/ClassicPress context, this cannot be achieved at all.
What are HTTP Security Headers and why you should care about it. Please tweet thisHow to add HTTP security headers to your website
The mandatory HTTP security headers should be added to the webserver layer by your hosting company, period. If this doesn’t happen, why are you using such careless hosting? It’s time to run from it.
To understand the situation, let’s explore more. There are three options for adding security headers to your WordPress/ClassicPress website:
- By your hosting company, straight in the webserver.
- By adding the rules in the .httaccess file.
- By a plugin.
Let’s dig deeper to understand these options better.
HTTP security headers are added by the hosting company, straight into the webserver
This is the recommended way.
Proper HTTP security headers are considered hygiene, a minimum good practice of any decent hosting company. Because they are added straight into the webserver, this is the fastest and simplest method. It is also the most robust. There is no way to misconfigure or accidentally disable. In fact, there is no way to disable even if your website is hacked.
On the other hand, when headers are added straight into the hosting server, they are always served from the fast RAM. This helps to keep your site as fast as it can be!
The only exception is the Content Policy header, which should be added by WordPress/ClassicPress admin.
What is the first security check you should make when choosing web hosting? Where do most hosting companies fail? Read this if you don't want to choose the wrong one. Please tweet thisEditing .htaccess
Editing of the .htaccess file should be done only by highly experienced admins, as even a small mistake can shut down your site, create vulnerabilities, or lead your website to not work as expected – or not work at all. For average users, this task is far too complex.
Because of such dangerous mistakes, some hosting providers do not allow users to edit .htaccess file. There is some logic here, as the smallest mistake can easily break the website or leave it unprotected.
Also, if the site is silently hacked, the hackers can simply disable protections by editing the .htaccess file.
Why adding HTTP headers to WordPress by plugin is a bad idea
The idea that plugins can solve all security problems in WordPress/ClassicPress is not the brightest one. Why?
Yes, it sort of solves the HTTP headers problem. Sort of.
But on the other hand, you just used a PHP plugin to solve the problem of an irresponsibly configured WordPress hosting server. Now your crucial security aspect depends on one more third-party code provider, which can be hacked or silently sold to bad people or face many other security concerns that wouldn’t have existed if the hosting company had added these headers to the hosting server.
Of course, if the website is silently hacked, these headers can be easily disabled, too.
Exception: The Content-Security-Policy HTTP header
Only the Content-Security-Policy HTTP header can be added with the help of a WordPress plugin.
If it doesn’t break your website, go for it, as it is a recommended feature. Write a content security policy and check it on the staging (development) site before activating it in production.
Also, if you really can’t disable plugins that break your website, you can use a specialized CSP headers management plugin. While requiring a lot of work, it is a recommended security measure.
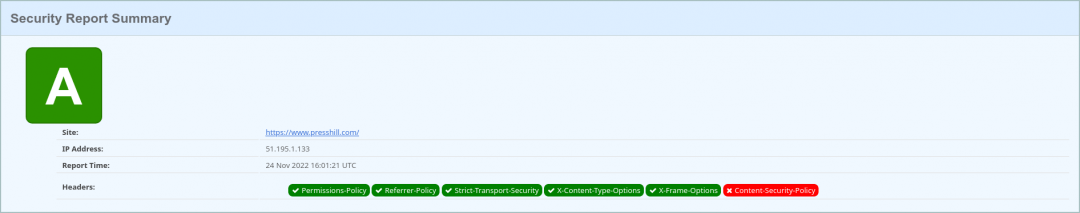
How to check security headers
SecurityHeaders is an excellent tool by security researcher Scott Helme.
While grades in site speed measurement services are generally useless, on this website they are accurate and useful.
Check your website, check your hosting provider’s website, andcheck websites where you enter your card number or any other sensitive information. All mandatory headers should be in the green range.
Why do many hosting companies not care about your security?
The four main security headers are not something advanced; they are just security hygiene. The WordPress hosting company, which cares about clients’ security, adds security headers to the hosting stack by default, period.
But why do so many hosting companies not do this?
We can presume that the answers are:
1. They don’t care about the client’s security.
2. They don’t have even a basic understanding of information security.
3. (The most common in our experience) Both of the above.
This is a dangerous double fail that we often see when a so-called “managed WordPress hosting” company fails to set up security headers. At first, they fail to properly set up their server, and then they fail to properly manage the WordPress site! But, of course, you will find every imaginable marketing blah-blah-blah about security on their website. Even if their own website fails to provide appropriate HTTP security headers.
Yes! The funny thing is that many hosting companies do not add these headers even on their own websites! That means it is dangerous to even buy hosting from such hosting providers, as when you enter your payment card number, you don’t know whether you are entering it into the original website or providing it to hackers. Remember, 39% of WordPress vulnerabilities are cross-site scripting(XSS) issues.
Does your hosting provider care about security headers? How to check and why it is so important? Please tweet thisTHE question is: If WordPress hosting provider fail in such an elementary but dangerous area, why should you expect that he care about more complex security measures? Do they understand security at all? Where else are they failing?
Run away from hosts that don’t have properly set-up security headers on their own websites!



Leave a Reply